About Threat Watch
In today's digital landscape, organizations face a constant barrage of cyber threats, from exposed credentials on the dark web to unpatched software vulnerabilities. The challenge is immense: security teams are often overwhelmed by disparate data sources, manual processes, and reactive firefighting, leaving critical gaps in their defenses. Threat Watch is the unified cybersecurity intelligence solution designed to solve this problem. It provides a clear, actionable, and real-time picture of your organization's cyber health by continuously analyzing assets, vulnerabilities, and exposures. Tailored for IT security teams, risk managers, and business leaders, its core value proposition is speed and clarity. Instead of sifting through endless alerts, Threat Watch automates assessments and prioritizes risks, enabling you to move from a state of confusion to one of control. It empowers you to proactively identify, understand, and mitigate threats faster than ever, transforming cybersecurity from a complex burden into a manageable, strategic advantage.
Features of Threat Watch
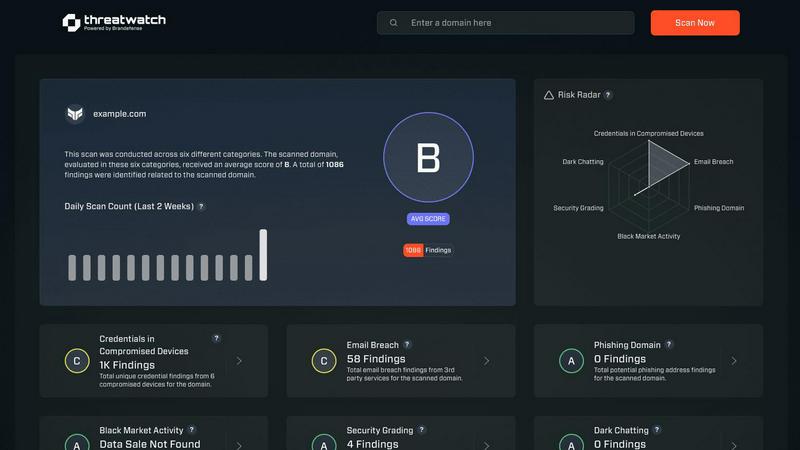
Comprehensive Cyber Health Dashboard
Threat Watch delivers a centralized, intuitive dashboard that synthesizes complex security data into a single, clear view of your organization's cyber health. It evaluates critical categories like compromised credentials, breached accounts, and vulnerable devices, providing an immediate, at-a-glance understanding of your security posture and where attention is needed most.
Real-Time Exposure Monitoring
Go beyond internal scans with continuous surveillance of external threats. This feature actively monitors the dark web, phishing databases, and breach repositories for your organization's exposed credentials, intellectual property, and sensitive data, alerting you the moment a new exposure is detected so you can act immediately.
Automated Asset & Vulnerability Assessment
Threat Watch automatically discovers and inventories your digital assets, from devices to cloud instances. It then continuously scans these assets for known vulnerabilities, misconfigurations, and security gaps, providing automated, prioritized assessments that tell you exactly what to fix first based on actual risk.
Prioritized Risk Mitigation Insights
Facing hundreds of vulnerabilities is paralyzing. This feature cuts through the noise by not just listing problems but providing context-driven prioritization. It correlates asset criticality, exploit availability, and active threat intelligence to deliver a clear action plan, telling you which risks pose the most immediate danger to your business.
Use Cases of Threat Watch
Proactive Breach Prevention
Instead of waiting for a breach to occur, security teams use Threat Watch to proactively hunt for stolen employee credentials and corporate data on the dark web. By discovering and resetting compromised passwords before they are exploited, organizations can prevent account takeover attacks and significant data breaches.
Streamlining IT Security Audits
Preparing for compliance audits or security reviews is a time-intensive manual process. Threat Watch automates the evidence gathering by providing continuous, documented reports on asset inventory, vulnerability status, and exposure levels, drastically reducing preparation time and demonstrating due diligence.
Third-Party and Supply Chain Risk Management
Organizations can extend their security monitoring to assess the cyber health of key vendors and partners. By understanding if a partner's breached data could impact their own network, companies can manage third-party risk more effectively and enforce stronger security requirements in contracts.
Executive and Board-Level Reporting
Security leaders need to communicate risk in business terms. Threat Watch translates technical vulnerabilities into a straightforward "cyber health" score and clear reports, enabling CISOs to provide executives and the board with concise, actionable insights into the organization's security posture and investment needs.
Frequently Asked Questions
How does Threat Watch discover my company's data on the dark web?
Threat Watch employs specialized crawlers and monitors a vast array of dark web forums, marketplaces, and paste sites. It uses sophisticated algorithms to search for your organization's domains, email addresses, and other identifiers, alerting you when matching credentials, internal documents, or other sensitive data are found for sale or leak.
What kind of assets does Threat Watch scan for vulnerabilities?
The platform performs non-intrusive, external scans to discover a wide range of internet-facing assets. This includes corporate websites, web applications, email servers, network infrastructure, and cloud service endpoints. It identifies these assets and checks them against known vulnerability databases for potential security weaknesses.
Is the free scan really free, and what does it include?
Yes, the initial scan is completely free and requires no credit card. It provides a snapshot assessment of your organization's exposure in key categories like breached credentials, phishing threats, and compromised devices. This gives you immediate value and insight into critical risks without any upfront commitment.
How does Threat Watch help prioritize which vulnerabilities to fix first?
Threat Watch uses a risk-based scoring model that goes beyond a simple severity score. It factors in the context of your specific environment, including how critical the affected asset is to your business, whether there is an active exploit available, and if the vulnerability is being discussed in threat actor communities, providing a true priority list.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt automates contract signing with secure templates and AI reminders to save you time.
aVenture
aVenture helps you research private companies and track competitors with AI-powered venture intelligence.